The Versatility of Application Security

Most security programmes base their findings on protecting core IT components, including networks, storage, PCs and servers, and data centres. So honing in on infrastructure is key, but it’s not the only part of a well-established information security programme.
Application security includes plenty of techniques that allow the process of finding, fixing, and stopping further exploitable vulnerabilities in application software. These techniques encompass the whole application lifecycle and include:-
- Code reviews are conducted by security professionals whose goal is to identify security vulnerabilities unique to the application.
- Black box security review based on using an application.
- Review application design, within the framework of a threat model, before writing any source code.
- Using automated test tools that are designed to locate and trace security vulnerabilities.
- Implement crowdsourced bounty programmes to leverage white hat hackers to identify and fix vulnerabilities before they can be taken advantage of.
The most valuable information security processes are modelled on layered security. A tiered approach provides defence in depth to halt and contain incursions by offering protective measures tailored to each type of asset.
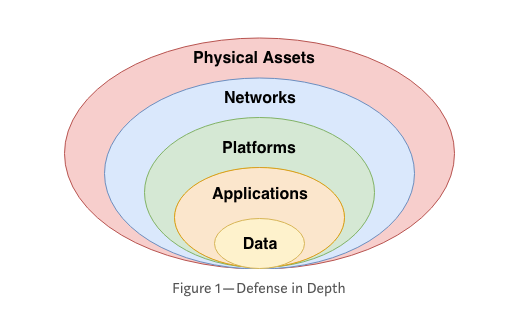
Considering the applications are one of the internal layers, it is logical to prioritise application security. It is also intelligent considering that applications are an externally facing component and give potential hackers a clear route into the system.
The frontend can weather the storm
Web applications have a high degree of exposure and risk since browsers are inherently unsafe. This is not an indictment of browsers; it is a statement of fact based on the architecture imposed by the execution environment. It is almost a rite of passage for new Web Developers to attempt and fail at securing data in the browser.
One susceptible area is the keys and secrets required for authentication with cloud-based services. For example, applications using the GitHub API must supply a token to identify itself as part of the authentication process. However, it’s vital to keep secrets private since, if compromised, a bad actor could use them to steal source code or vandalise a repo.
The Lure of Frontend Security
A myth that frontend developers often fall for is believing that they are secure by implementing secretive measures such as private keys and tokens outside the source code. However vital it may be for application secrets to be kept outside these parameters, they are not locked up if the client runs in a browser.
Here is one technique used to separate data from source code, and how straightforward it is to believe this wholly protects you.
Environment variables externalise data by moving it from the source code into a file, like the .envfile. The additional step of adding this file's name to .gitignore prevents git push commands from uploading it to the GitHub repo where, for public repos, it could be accessed by anyone.
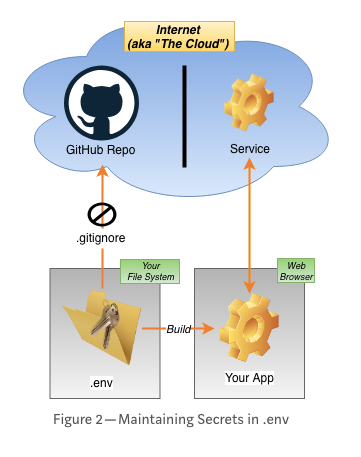
It is crucial to look at the whole picture of your application security processes and not be fooled into any easy fixes or quick wins.
