Welcome to the Tutamantic Security Blog!

The Tutamantic team is eager to provide short articles on real-world tips, tricks and guidance on how to execute on good application-design security practices. This has led to the birth of this blog.
Threat modeling is still considered by many to be an overbearing, manually-intensive and difficult activity. Tutamantic is here to change that!
Let's kick off the ideas with a post on what is the most important security control pattern to enable secure software systems. If we look at STRIDE (https://en.wikipedia.org/wiki/STRIDE_(security)) as a simple abstracted model of threat patterns, which one is arguably the most dangerous?
The way to think about this is to look at each threat pattern and deduce if that pattern can easily invoke any of the other patterns. For example, if you cause a Denial-Of-Service can that in turn cause anything else? The one threat pattern that can cause any of the other threats is Elevation-Of-Privilege. It is probably the most dangerous attack vector and the one which will cause the most damage if not properly mitigated against. It can easily cause any of the other STRIDE elements once achieved. Elevation-Of-Privilege is otherwise known as Command-And-Control in an attack kill-chain (https://en.wikipedia.org/wiki/Kill_chain).
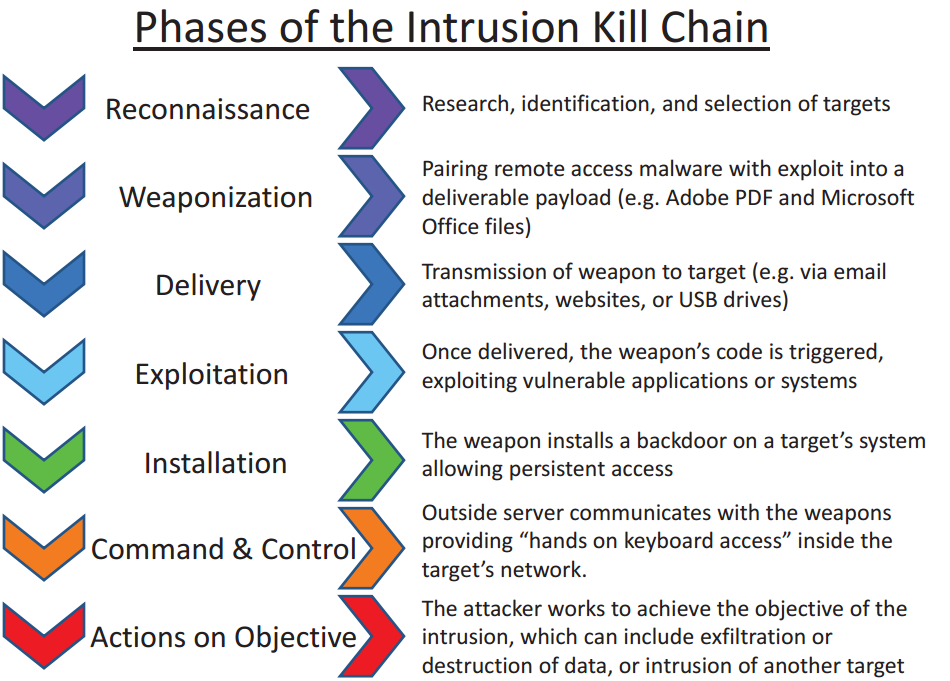
Command-And-Control is the one element in the kill-chain which allows the attacker tactical latitude and the freedom of movement across a victim's system.
So any threat modeling technique should put the discovery of access control and authorization threats (aka Elevation-Of-Privilege, Command-And-Control) as a primary approach.
